Fake Access Point with Airsnarf
As you know wireless hotspots are everywhere. A mobile user can obtain connectivity quickly and easily in a wide variety of public locations. Some of these hotspots are free and some of them require a fee or subscription. Either way, you will continue to see how being in a public Wi-Fi hotspot poses the greatest security risk you will find.
Stealing Wi-Fi Hotspot Subscription Credentials
A big issue a few years back had to do with dial-related fraud in Russia. Basically, usernames and passwords to dial accounts were being bought and sold on the black market and the owners of the stolen credentials were being hit with enormous usage charges. In actuality, this still takes place. With the onset of Public Wi-Fi locations, the threat of fraud and misuse has also moved to the stealing of wireless subscription credentials.
An easy and inexpensive method to steal wireless subscription credentials is by Access Point Phishing. As it stands today, the only real methods a typical end-user has to determine if a wireless access point is valid is by recognizing the SSID (name of the wireless network) and ascertaining if the site has the look and feel of the real public Wi-Fi hotspot login page. Unfortunately for the end-user, both of these can be easily spoofed. Here’s how it’s done and no, you won’t have to carry a wireless access point around to do this.

Performing this technique requires two steps:
- Setting up your computer to look like an actual Access Point broadcasting the appropriate SSID
- Having the walled-garden, or login page that your computer will display look like the real login page of the provider whose signal you are broadcasting
It’s not hard to make your computer broadcast the SSID of your choice, in an attempt to get a person to connect to you instead of a valid Wi-Fi hotspot SSID. The problem with the ‘easy way’ is that the potential victim sees that this is an Ad-Hoc network and most people these days know not to connect to these. So, we employ the use of Airsnarf by the Schmoo Group to make this signal look like it’s coming from an Access Point. Essentially, we will be turning the laptop into an Access Point.
The most difficult part of using Airsnarf and other HostAP (Host Access Point) reliant programs is finding a card that supports the HostAP drivers. Airsnarf consists of a number of configurable files that control how it operates.
Where to get Airsnarf
BackTrack (BT) is a live CD based on Slax, hence Slackware, it is evolved from the widely adopted Whax and Auditor security distributions.
Slackware is one of the many Linux distribution, Slax is a linux live-distro version based on Slackware. BackTrack is a Penetration Testing oriented live-distro based on Slax.
BT has an intuitive layout, some tools are available in the menu and invoke automated scripts, most of the analysis tools are located either in the path or in the /pentest directory. It is possible to explore wireless tools under /pentest/wireless.
Airsnarf is located at /pentest/wireless/airsnarf-0.2
Using Airsnarf
airsnarf.cfg file used to configure basic Airsnarf functionality
dhcpd.src file can used to configure the DCHP settings of the access point created.
With Airnsnarf configured with default design settings, it will display a default login page that looks like the following. To make this attack really work, this login page needs to be modified to look just like a real Wi-Fi hotspot provider’s login. Depending upon your HTML skills, you can either get real fancy or just stick to basics.
Once Airsnarf is configured and the customer Login page is created, the attack can be launched. Any airport, coffee shop, or other public area where people utilize their laptops will work. To launch the attack, activate Airsnarf by typing the ./airsnarfcommand. Below is an example of what you’ll see when the attack is launched.
Airsnarf being launched and waiting for a connection
An end-user attempting to connect to the hotspot will see the SSID that was entered into the airsnarf.cfg file and use their computer to connect to that network. Upon launching their browser, they will be prompted to enter their username and password.
Windows Zero Config showing the KYRION HotSpot being broadcast by Airsnarf
Once the user enters their credentials and hits the Login button, their credentials have been compromised and can be used by the person with ill-intent. This could be only the beginning, though. Commonly, users will utilize the same username and password for many different accounts/websites. Consequently, the username and password that were just grabbed may enable a hacker to access the user’s e-mail, online banking, etc.
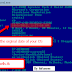
This login page will take the username and password that is entered and will dump them into a file where it can be read.
Example of credentials entered into Airsnarf AP Phishing Site and dumped to a file
Preventing Attack
There are basically two things to combating the previous hacks:
- Taking measures to ensure a hotspot is valid
- Protecting the machine against browser-based exploits